![]() In the event of a security incident, our Rapid Response Force is available 24/7.
In the event of a security incident, our Rapid Response Force is available 24/7. ![]()
Identify vulnerabilities in your systems with penetration testing
A penetration test is a method of assessing the security of an information system or application. It involves simulating the behavior of an attacker on the offensive, right up to the actual exploitation of security flaws, with a view to proposing a plan for improving IS security.

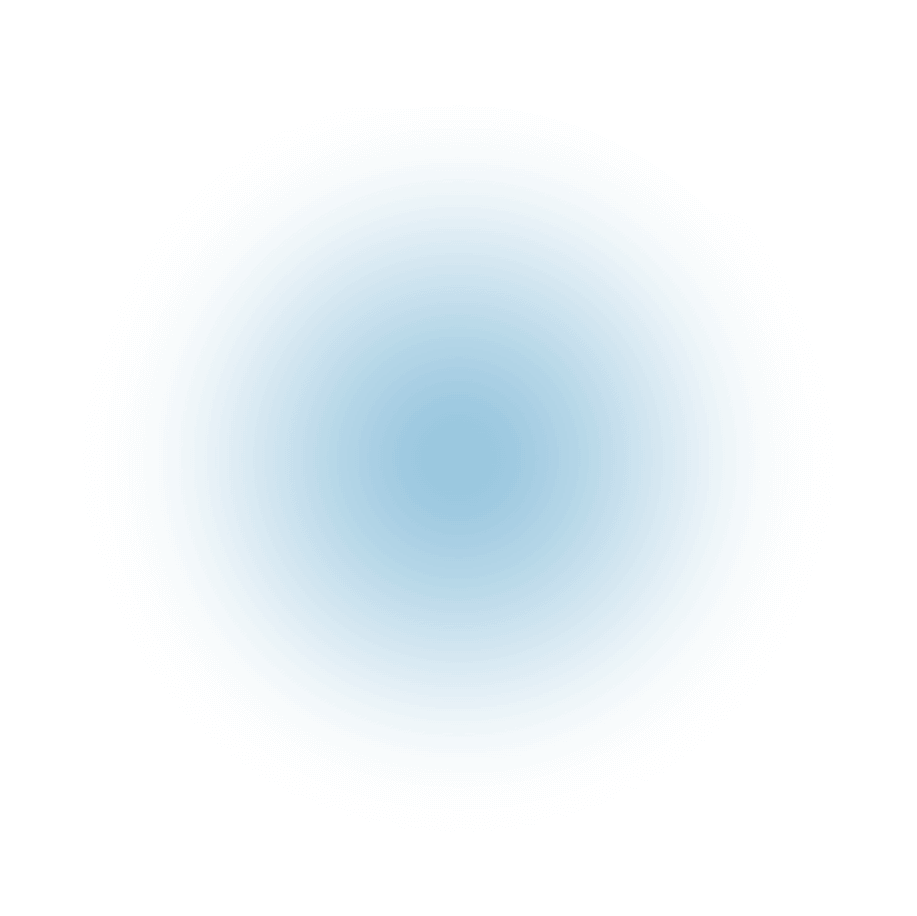

32 %
Exploitation of vulnerabilities remains the 1st vector of infection, accounting for 32% of attacks.
Incident response analyst report – 2021
Get an overview of the technical security level of an IS or application
Prioritize efforts on what’s really important! A challenge for our customers with limited budgets, sometimes scattered skills and equally limited time.
Our penetration testing experts put their skills at your service to identify vulnerabilities and highlight realistic compromise scenarios. They then classify the commercial and business impact of their presence in the IS. With this risk-oriented perspective, our auditors then build the technical roadmap for optimized impact mitigation.

The different perimeters on which to carry out an intrusion test
Web applications & APIs
For marketplaces, recruitment sites, e-commerce, CMS, CRM, customer areas, showcase sites… our auditors identify vulnerabilities across the entire application chain: from the front end to the server.
For APIs, in REST or SOAP, we identify vulnerabilities enabling the system hosting the API to be corrupted, data to be manipulated illegitimately, or rights/identities to be usurped.
IT & OT internal network
Our mission is to detect vulnerabilities that could compromise part or alĺ of the company’s internal network: Stations, Servers, Active Directory, Citrix…
Regarding OT (Operational Technology), our experts identify vulnerabilities that could break the isolation of the OT network, compromise equipment and theoretically interfere with scheduled cycles, with particular attention to avoiding any denial of service on these often-fragile systems.
Mobile applications & fat clients
Whether iOS, Android or fat-client applications, we identify vulnerabilities by reverse engineering the application, analysis of libraries and API used.
The audit takes place in two phases, with a “static” part where the analysis is carried out on the binary, and a “dynamic” part where the application is analyzed while it is running.
Cloud infrastructure
Here, our mission is to detect vulnerabilities specific to the deployment of an infrastructure in the Cloud, whether AWS, Azure or GCP.
A competent team on a human scale
A PASSI-qualified company
Formind has been qualified PASSI RGS audit provider by ANSSI since January 2019, and on all 5 scopes since 2021. Each of our services benefits from PASSI procedures and expertise, particularly regarding customer data confidentiality.
A multi-certified team
Our pentesters are at least OSCP-certified. For more senior staff, OSEP, OSED and OSWE certifications complete their profiles.
Most of our pentesters are personally active as hunters on Bug Bounty platforms.
A team on a human scale
With a team of around 15 pentesters based in Paris, Rennes and Toulouse, our team works closely with our customers, acting as a real partner over the long term.


FAQ
How long does a typical penetration test take, and when should we schedule one?
The duration depends on the size and complexity of your infrastructure. In general, a penetration test can last from a few days to a few weeks. It is recommended to schedule regular tests, especially after major system upgrades or infrastructure changes.
How do we ensure data confidentiality during penetration testing?
We strictly respect confidentiality and security standards. All sensitive data is treated with the utmost confidentiality.
What happens after the penetration test, and how can you help us remediate the vulnerabilities detected?
After testing, we provide a detailed report of all detected vulnerabilities, categorized by risk level. Then, we work with your team to develop a technical roadmap to effectively remediate these vulnerabilities.
Let's stay in touch
Our experts can provide you with ongoing support for your cyber issues. Do you have a question? You’ve come to the right place, and we’ll get back to you within 24 hours!
